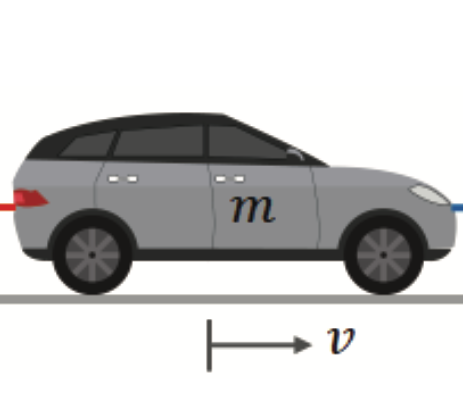
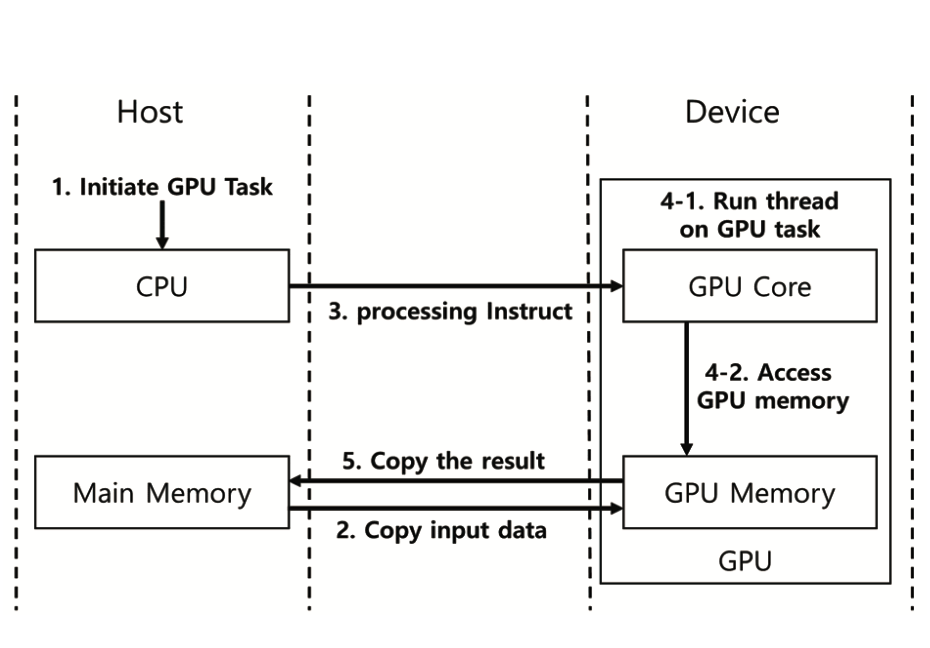
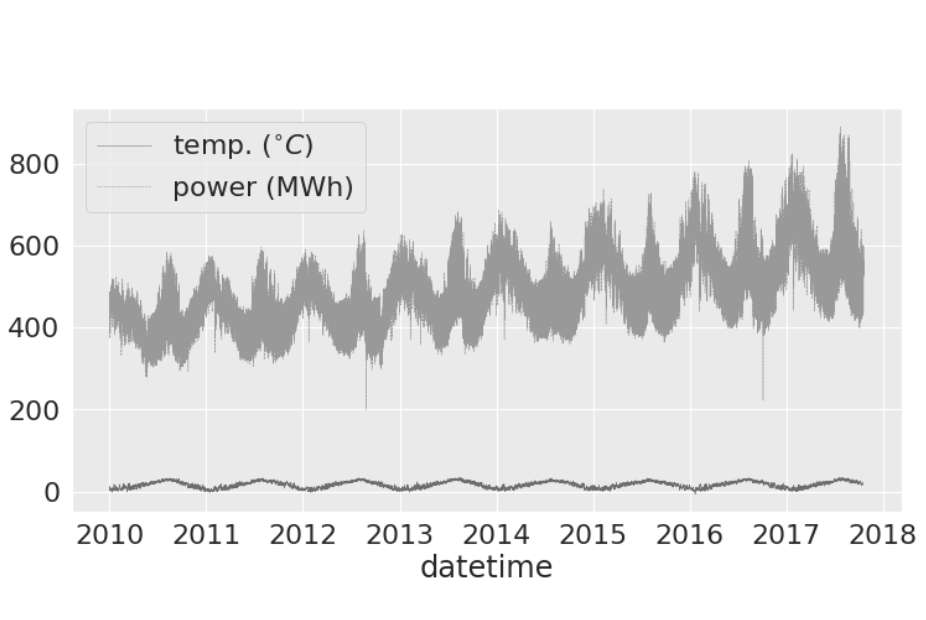
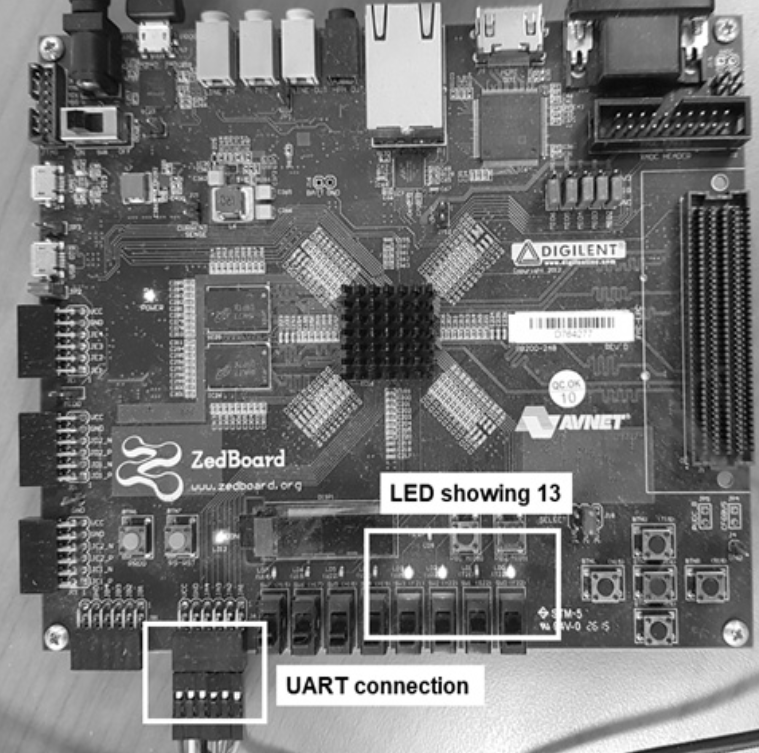
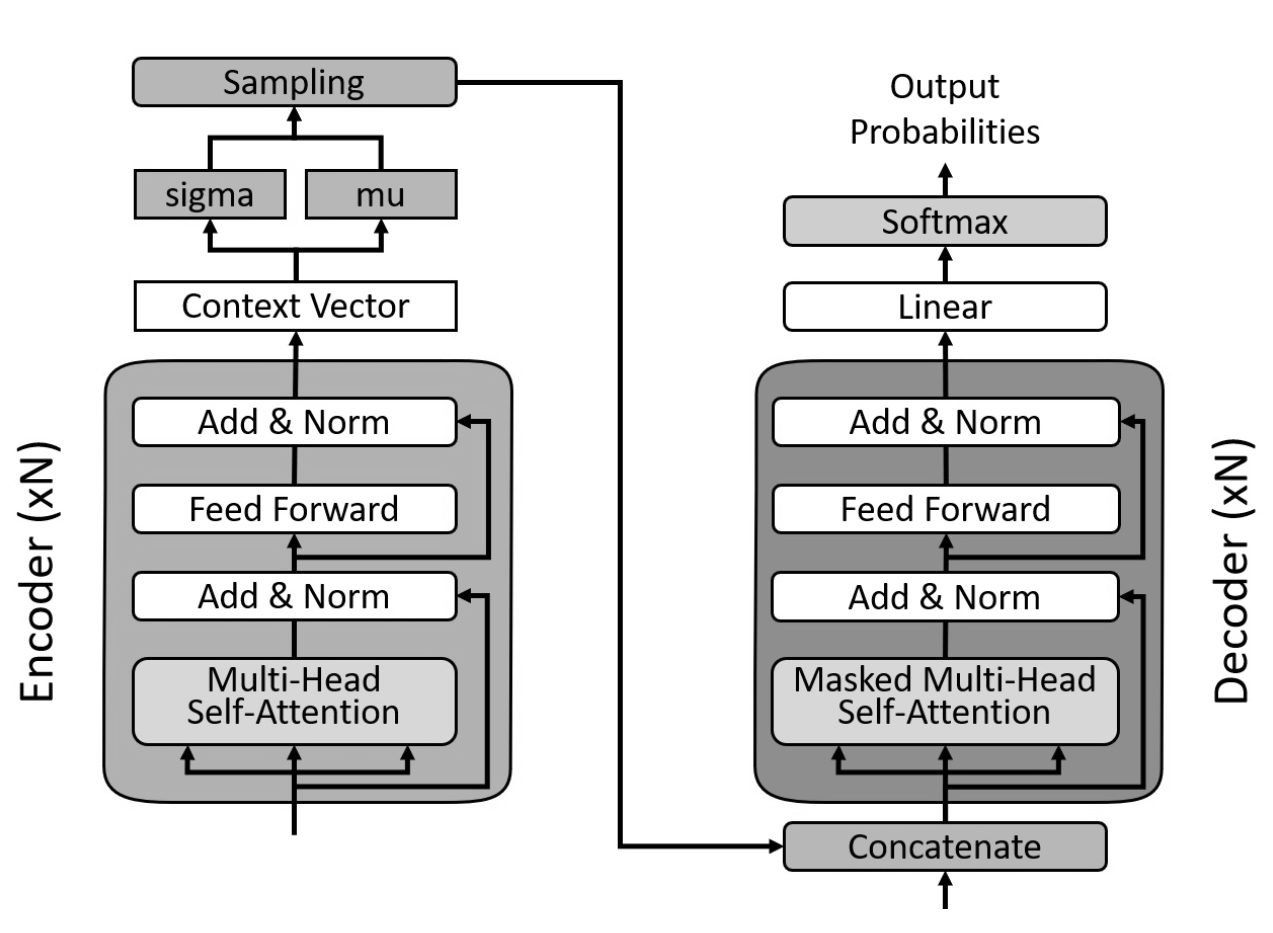
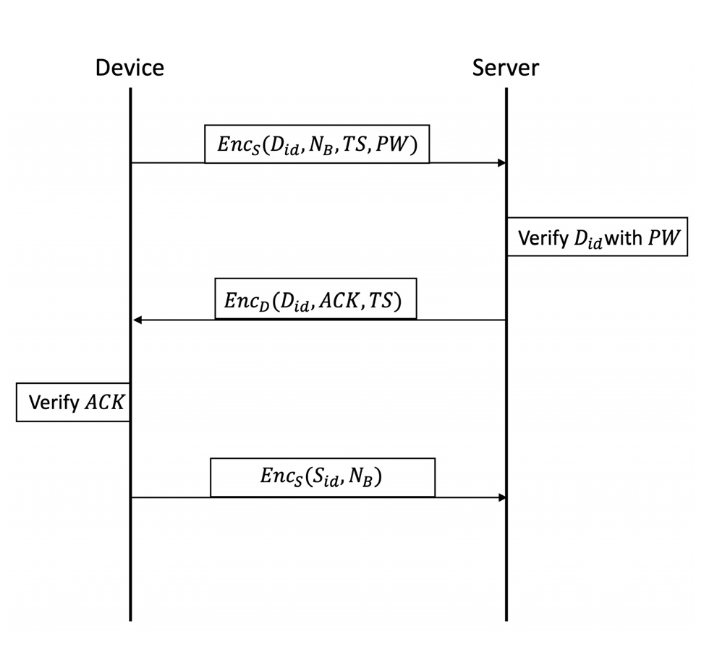
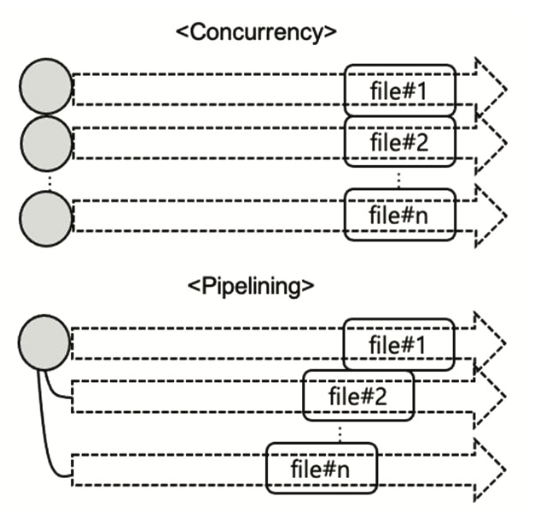
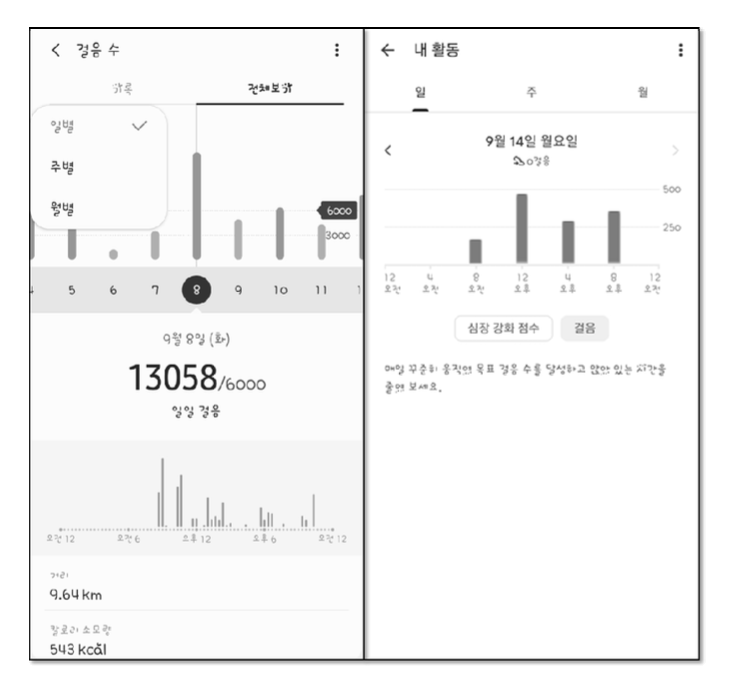
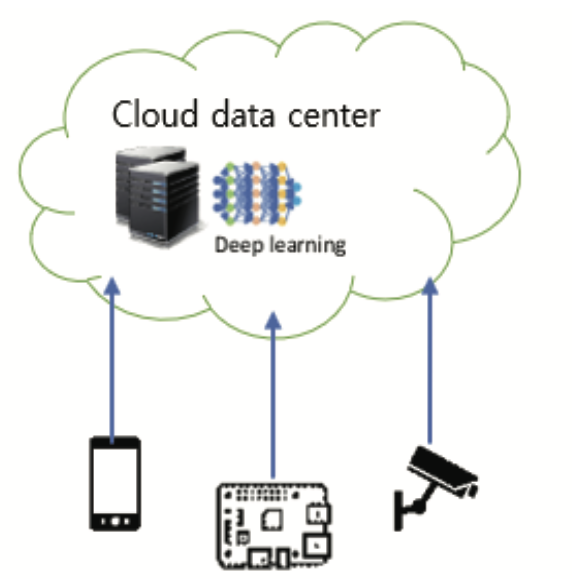
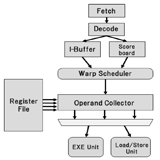
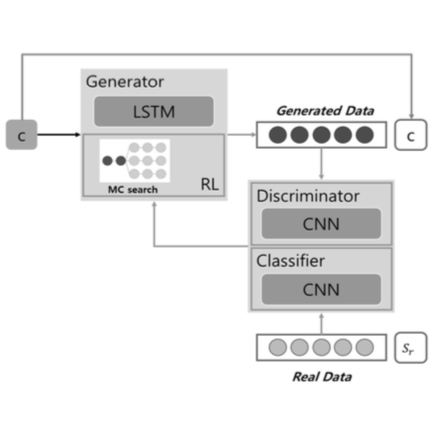
Second Half of 2023
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
First Half of 2023
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
Second Half of 2022
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
First Half of 2022
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
Second Half of 2021
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
First Half of 2021
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
Second Half of 2020
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
First Half of 2020
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
Second Half of 2019
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
|
|||||||||||
First Half of 2019
|
|
||||||||||
|
|
||||||||||
|
|
||||||||||
|
|||||||||||


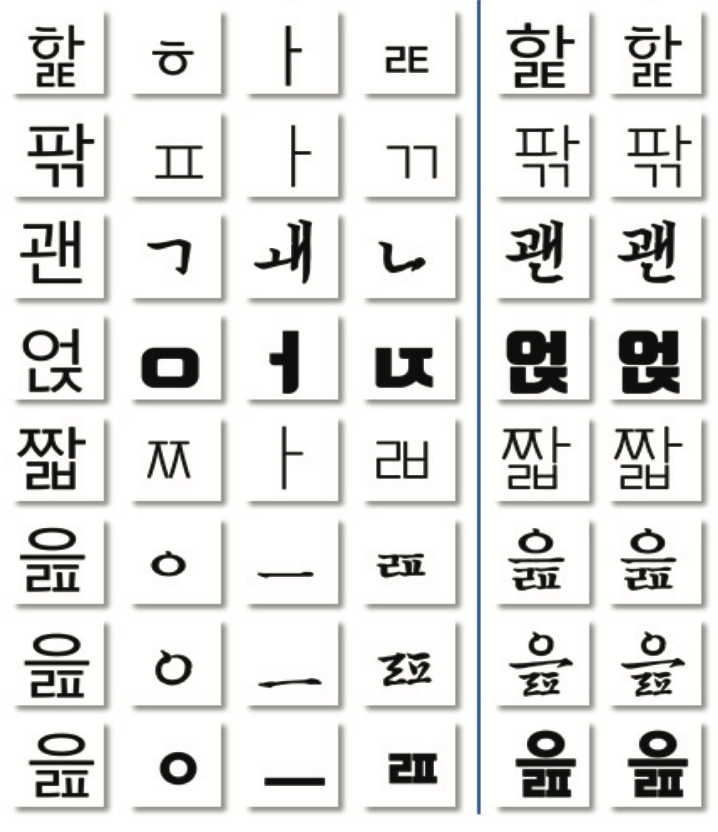
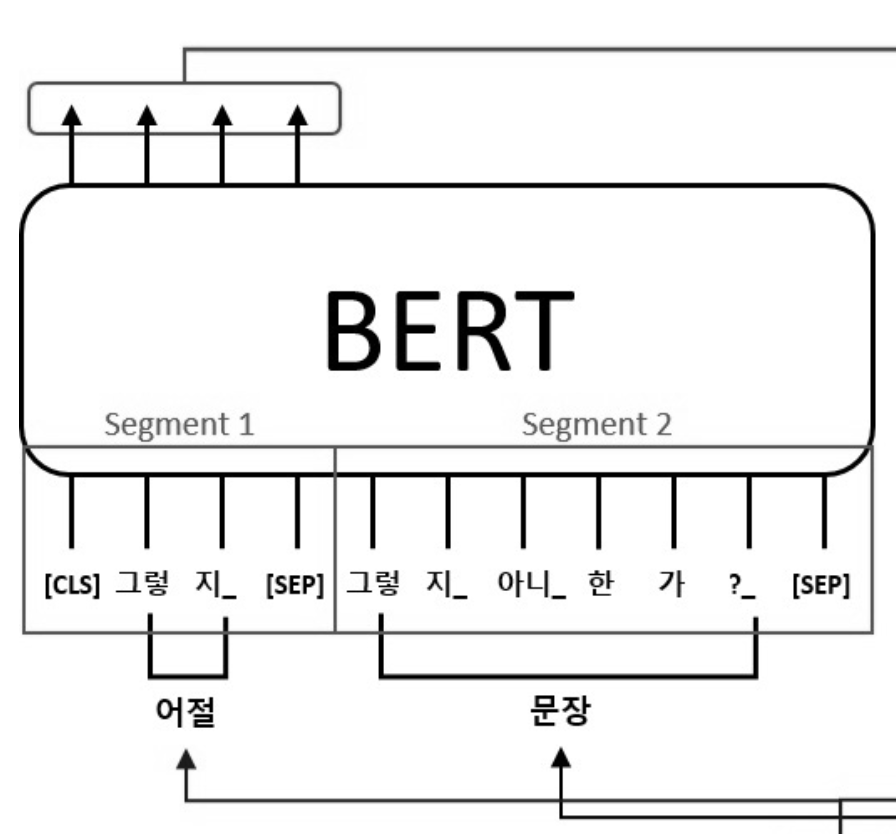
 Korean
Korean